To implement virtual network-to-virtual network connectivity, you need to go through a series of steps. These steps are relevant for establishing the connection. The following are the steps required:
- Create virtual networks and subnets: You need to set up your virtual networks and subnets to host the workloads.
- DNS server: This is an optional step; you can skip this if name resolution is not required.
- Create gateway subnet: Before you deploy the VPN gateway, you need to add a dedicated subnet to the virtual networks you want to connect. This subnet is for hosting the VPN gateway instances, and a CIDR block of /27 or /28 would suffice. The name of the subnet should be GatewaySubnet.
- Create connection: You need to create a connection from the VPN gateway.
The process outlined is the same for on-premises except there is a slight change in the connection setup. Nevertheless, you will get to see that later in this chapter. Let’s perform an exercise to connect virtual networks using VPN gateways. In Figure 4.10, you can see the infrastructure that you need to deploy for testing the VPN connectivity. You will have two virtual networks, vnet-01 and vnet-02, created in East US and West US, respectively. The virtual network vnet-01 has three subnets, namely, jumpboxSubnet, workloadSubnet, and GatewaySubnet. The jumpboxSubnet will host the jumpboxVM that will be used to access the vm-01 that is deployed in workloadSubnet. You have workloadSubnet in vnet-02, which will host vm-02. Both virtual networks will contain a GatewaySubnet for hosting VPN gateway.
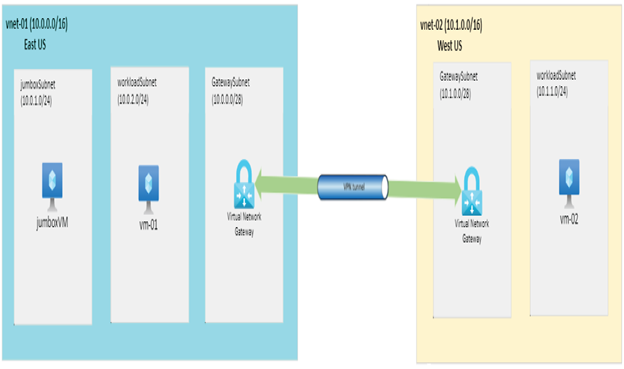
FIGURE 4.10 VPN demo infrastructure
You can deploy the resources shown in Figure 4.10 one by one because you have seen the deployment of each of these resources in the previous chapters except the VPN gateway. You can also use the PowerShell script added at the following location to deploy the infrastructure easily:
https://github.com/rithinskaria/azure-infra/blob/main/vpn-infra.ps1
If you have completed the infrastructure deployment, then you can start Exercise 4.2 to implement the VPN gateway connection. Once the PowerShell script is executed, it will return the FQDN to connect to the jumpboxVM and private IP addresses of vm-01 and vm-02, respectively. If you are deploying manually, please note these values as you need them during the exercise.
EXERCISE 4.2
Implementing the Virtual Network to Virtual Network VPN in the Azure Portal
- If you have successfully run the PowerShell script, all resources will be deployed. SSH to the jumpbox VM using the FQDN returned by the script.
- From the jumpbox VM, SSH to vm-01 using the command ssh 10.1.1.4.
- Once you are logged in to vm-01, try pinging vm-02. This will fail as you haven’t set up any method to let these two virtual networks communicate with each other. In Exercise 4.1, you established the connectivity using peering, and here in this exercise, you will set up the connection using VPN gateways.
- Let’s deploy a VPN gateway to the GatewaySubnet of vnet-01 from the portal. Navigate to the Azure portal and search for virtual network gateways. Click Virtual Network Gateways; this will take you to the page where you can create the gateway.
- Click + Create to start the creation process; the following inputs need to be provided:
- Subscription: Select the subscription where you have deployed the virtual networks.
- Resource Group: This will be automatically selected based on the resource group of the virtual network.
- Name: Provide a name for the VPN such as vpn-eus.
- Region: Set this as East US as vnet-01 is deployed in East US. You need to make sure that you select the same region as the virtual network.
- Gateway Type: VPN.
- VPN Type: Route-based.
- SKU: VpnGw1.
- Generation: Generation 1.
- Virtual Network: Select vnet-01; the gateway subnet will be automatically selected.
- Public IP address: Create a new public IP address.
- Public IP address name: Provide a name for the public IP address.
- Enable active-active mode: Disabled, as you are not configuring active-active mode.
- Configure BGP: Default value, disabled.
Leave a Reply