- Once you have entered all the inputs, click Review + Create. This process will take 30 to 45 minutes.
- In the interim, you can create the second gateway for vnet-02 in West US. Now, you will use PowerShell to create the gateway as you are already familiar with the process in the portal.
- Create a public IP address using the following command:
$gwpip= New-AzPublicIpAddress `
-Name pip-vpn-wus `
-ResourceGroupName vpn-demo-rg `
-Location ‘West US’ `
-AllocationMethod Dynamic
9. Once the public IP is created, go ahead and create the VPN gateway by using the following command:
$vnet = Get-AzVirtualNetwork `
-Name vnet-02 `
-ResourceGroupName ‘vpn-demo-rg’
$subnet = Get-AzVirtualNetworkSubnetConfig `
-Name ‘GatewaySubnet’ `
-VirtualNetwork $vnet
$gwipconfig = New-AzVirtualNetworkGatewayIpConfig `
-Name vpn-wus `
-SubnetId $subnet.Id `
-PublicIpAddressId $gwpip.Id
New-AzVirtualNetworkGateway `
-Name vpn-wus `
-ResourceGroupName vpn-demo-rg `
-Location ‘West US’ `
-IpConfigurations $gwipconfig `
-GatewayType Vpn `
-VpnType RouteBased `
-GatewaySku VpnGw1
- As mentioned earlier, this deployment will also take 30 to 45 minutes to complete. Once the VPN gateway is deployed, you need to create the virtual network to virtual network connection.
- Navigate to Virtual Network Gateways, select vpn-eus (gateway deployed in East US), and click Connections. Select + Add.
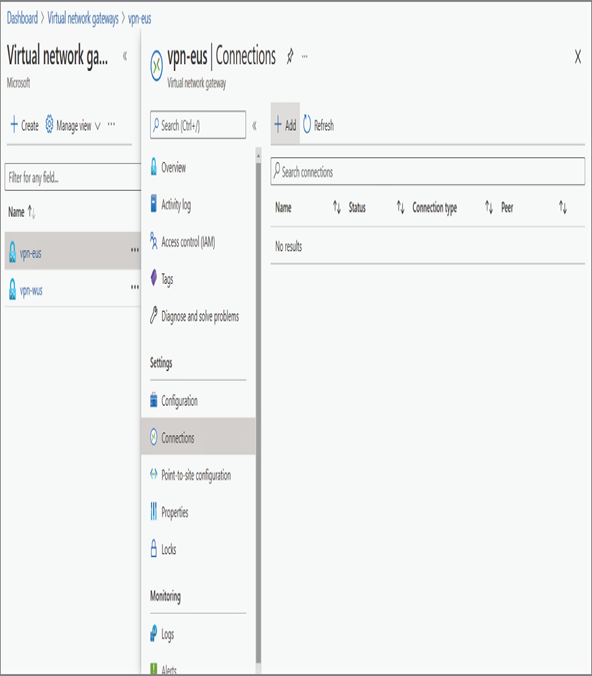
12. You need to add the connection details as follows:
- Name: Name the connection. Since you are connecting from East US to West US, give a name like eus-to-wus.
- Connection Type: This will be virtual network to virtual network, as you are connecting virtual networks.
- First virtual network gateway: The East US gateway will be automatically selected, and you cannot modify this.
- Second virtual network gateway: Select the virtual network gateway deployed in West US.
- Shared key (PSK): This is a combination of letters and numbers, used to establish encryption for the connection. The same shared key must be used in both the virtual network gateways.
- Use Azure Private IP address: Leave this unchecked, as this option is only available with AZ VPN SKUs.
- Enable BGP: Leave this unchecked, as you are not using BGP.
- IKE Protocol: Select IKEv2.
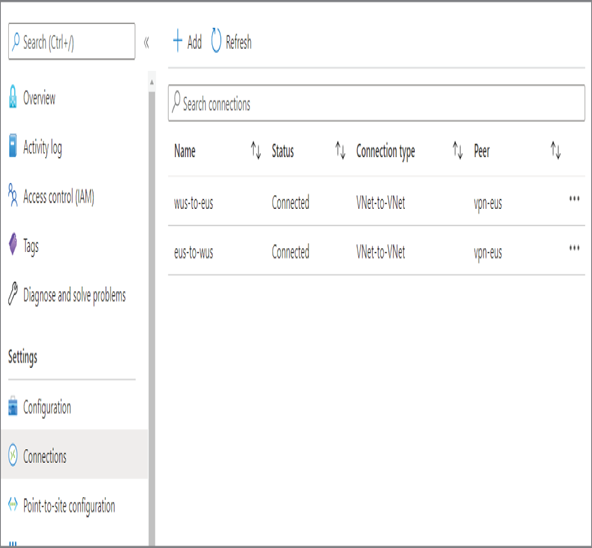
- Once these details are filled in, click OK. You will be able to see that the connection is added, and it’ll be in the updating state. Since you haven’t configured the reciprocal connection on the West US gateway, soon the status will change to Unknown.
- Navigate to the West US gateway and click Connections. In Connections, you will be able to see the eus-to-wus connection with a Not Connected status. Follow the same process outlined in step 12 and create a connection from the West US gateway to the East US gateway.
- After adding the connection, within a few minutes, the connection status will change to the connected state for both connections.
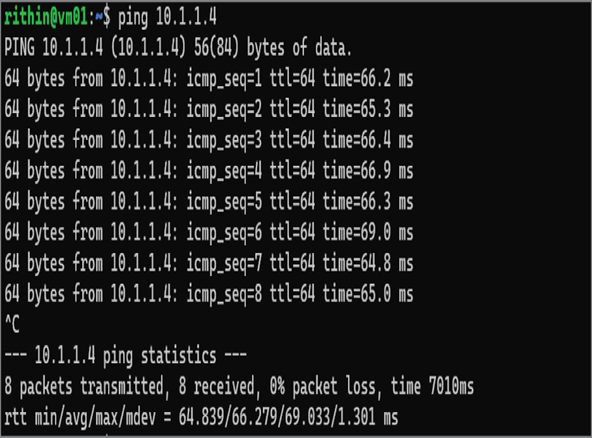
- Now, you will SSH to jumpbox, and then from jumpbox VM you will SSH to vm-01.
- From vm-01, try to ping the private IP address of vm-02, and the ping will work.
If your gateways are in two different subscriptions, then you need to use PowerShell for establishing the connectivity. You can follow the steps mentioned here to connect the gateways:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-vnet-vnet-rm-ps
With that, you will move on to compare the virtual network peering and VPN gateway to understand the difference between these two implementations though they serve the same purpose.
Leave a Reply